CMMC Boundaries
With version 1.0 of the Cybersecurity Maturity Model Certification (CMMC) having been signed, companies are beginning to scramble to understand what the requirements are and to prepare for certification. As the CMMC Accreditation Body sorts out who the Assessors and Third-Party Assessment Organizations (C3PAO) will be and to develop training and guidance, DoD contractors are determining what CMMC level certification they will need to achieve and when. Once those questions are answered, the next question companies should ask themselves is what needs to be protected?
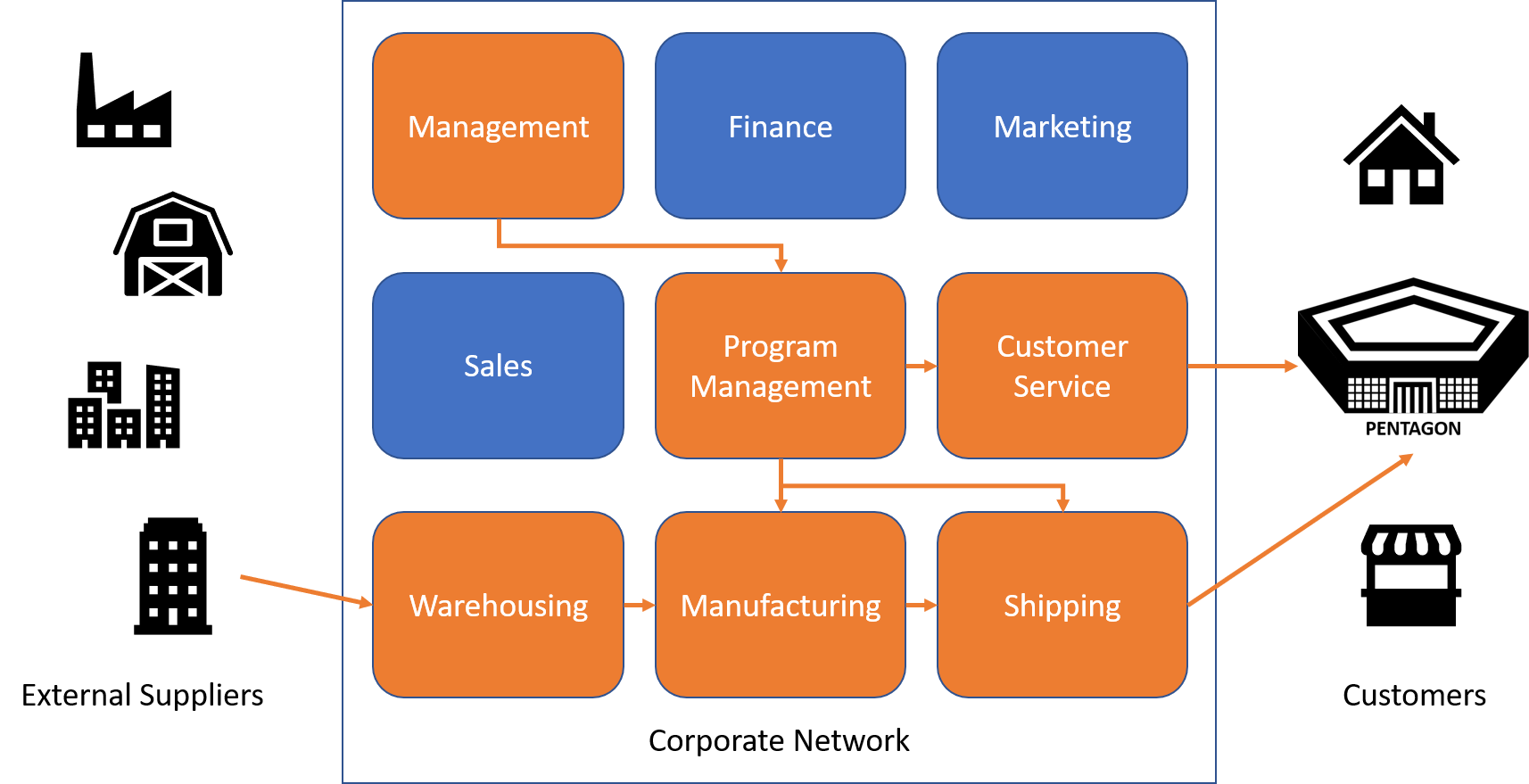
What are my certification boundaries going to be? Only the systems that handle government information, whether it be Federal Contract Information or Controlled Unclassified Information (CUI), need to be protected and certified. In the example below a company with multiple suppliers, divisions and customers, need only protect the systems that support the affected business processes.
Although securing and certifying your entire network would be the best solution, not every company can afford the time and cost to do so. A more affordable alternative to the example shown above would be to further segment your systems that need protection as depicted below and focus your resources specifically on those.
A third, and arguably the fastest and most affordable solution, would be to create a secure cloud environment as shown below, and conduct all your DoD contract related business there, away from your corporate networks.
So, when you start unraveling CMMC v1.0 take heed to focus your planning efforts on what needs to be secured, if the task seems impossible contact us at Ascolta, we specialize in the third option. Ascolta provides NIST SP 800-171 compliant cloud environments, designed to protect customer data to DFARS 252.204-7012 standards. Our environments are CMMC ready and will help you achieve the Good Cyber Hygiene rating (Level 3) required for contracts involving CUI. We provide our customers with the secure environment and necessary security documentation to include policy templates and completed Systems Security Plans. By utilizing our compliant environments, customers can achieve CMMC certification within days, allowing them to bid and win DoD contracts.